These are the notes of a full day talk about security from an attackers and defenders perspective. The talk was structured using the Killchain method. After each stage they have been shown how you could defend the specific weaknesses with a Cisco product. These articles are just notes and may be missing some specific context or could be already outdated.
The type of attacks were focused on:
- Ransomware
- DDoS
- APT (Advanced persistent threat)
Ransomware
Mostly victims get infected via web or email. Ransomware started to came up with Bitcoin. It was an easy way for the attacker to earn money. They try to keep anonymous with connections using mostly TOR or TOR DNS.
An Ukraine account software vendor got infected with Nyetya. It was a destructive ransomware variant that targeted different organizations inside Ukraine. To read more about this attack, checkout the Blogpost from TALOS: The MeDoc Connection
Attack Vectors
Mostly these two vectors are used for ransomware:
What possibilites do you have to defend against E-Mail based ransomware:
- Check SPF, DKIM, DMARC
- Anti Spam Filter
- Signature based AV (for example: Sophos, McAfee, TrendMicro)
- Nextgen Mail Protection using sandboxing and other features next to signatures. (for example: Cisco AMP)
Advertising
There is a huge market of companies for ads. You can't decide if it's a good or bad ad shown in your browser. To visualize to how many third party, most of them for ads, you connect, you can use Lightbeam. It's an addon for Firefox, which can visualize the connections done by your browser while surfing the web. After installation, open it and in another tab call an URL of your choice. Very interesting are news websites. You will see a bunch of connection to many other URLs. So these calls are third party pages you indirectly visit. Here you can get the Addon: Lightbeam for Firefox
Here's an example from the NY Times website. On the left without ad blocks and on the right with ad blockers (uBlock Origin and uMatrix)
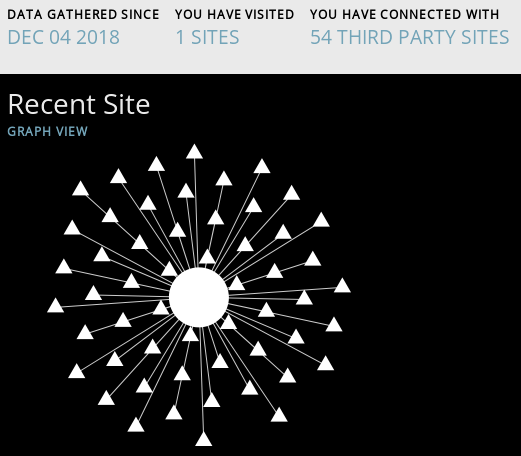
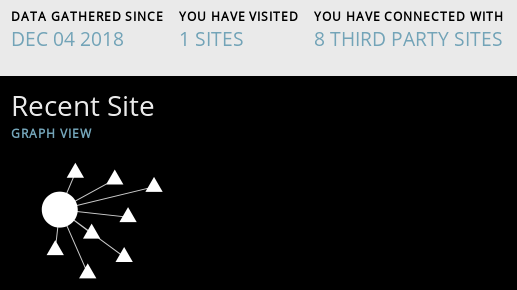
Ransomware Defense
DNS is you first layer of defense. When you can controll the DNS requests in your network, it is possible to detect malicious DNS requests and control what your DNS server will be reply to the request. If you can stop bad DNS requests, your clients don't even reach their destination for a successful infection.
Next to DNS, there should always be a Web Proxy in place to detect and be in control of the requested URLs from the clients. As always, don't forget the firewalls. They are very helpful for detection of malicious connection and to block them.
Summary for Ransomware defense:
- Email Security
- DNS Security
- Web Security
- Anti-Virus / End Point Security
- User Eduction
- OS/App Hardening (including patching!)
DoS and DDoS
Why could you hit by DDos?
- Financial reasons
- Political statements
- Hacktivism
- Cover for targeted attacks
- Reconnaissance against:
- DDoS Solution
- Service Provider
Types of DDoS attacks:
- Reflection
- Amplification
Reflection
A Reflection DDoS makes use of a Botnet and a faked IP packet. The reflection in this scenario is that the answer to this IP packet is not send to the real origin than to the victims IP.
For example: Put the IP address from your victim as source IP to an request and send this request to thousands of other IPs (your Botnet for example). Every bot of your Botnet will answer this request and send the answer to your victims IP address.
Amplification
Amplification attacks are a missuse of how protocols work. For example: SNMP sent 87 bytes and 60 KB are sent back as reply.
IoT
IoT: The S stands for security. Most of the IoT devices have:
- Internet Access
- Using a striped down Linux
- Are low margin devices
They are perfect target to build up a botnet which then can be used for DDoS attacks.
Mirai was the first malware that spread eplicitly to IoT devices. More about you see on the Defcon talk from Steinthor Bjarnason: DEF CON - The call is coming from inside the house
Solution
Talk with your Internet / Cloud Service Provider for solutions. For example: OVH and Cloudflare or only two that offers protection against DDoS attacks.
APT - Advanced Persistent Threat
These are the most advanced attacks with a lot of money and ressources behind. Mostly it's a nation-state behind the attack. They use multiple versions of the kill chain. To understand every step in the kill chain helps the defender to understand the bascis of an APT attack.
The free and available tools are usually few years behind the ones from an (APT) attacker!
Reconnaissance
This phase is here to gather as much information as possible from the target.
- Employees
- DNS
- WHOIS
- IP Ranges
Search for Information from the employees: tech forum, social media and so on.
One example of a way for recon: Google Hacking Database
Physical reconnaissance
- Coffee Machine talks
- Sneak in behind someone
- WiFi Protection
Defence against Reconnaissance
What can you do against the first stage of the kill chain?
- DNS protection
- Test google hacking on your own organization
- User Education
- Data classification
Gaining Foothold
The second phase is to enter the targets network. This can be done in multiple ways.
Physical Attack
Not always top of mind for employees is tailgateing. Teach employees and then check it with people trying to tailgate. :-)
PEAP-MSCHAPv2 with AD passwords is still dangerous for spear-phishing e-mails with a fake login website to grab the login of an employee.
Defense Summary:
- Use L2 Authetication always with certificates
- Teach your employee's
Client Compromise
Macros are hard to stop. There can be a web download from a csv file which includes the bad command; for example: powershell.exe ....
In Powerpoint a mouseover can be enough to start a macro to do evil stuff with it.
There are a lot of other options as well.
Defend against Client Compromise
Find cousin domains with kinda the same name who try to fool victims:
python dnstwist.py -g- m -r cisco.com
dnstwist checks if there are MX entries, active, registered and so on. If so start further steps to protect yourself from this maybe malicious domain.
Prevent against email spoofing with SPF, DKIM and DMARC.
Traditional Security systems needs to be in place as well:
- AV + Host-based IPS block 30%
- Metadata to what was run (CLI logs for ex.)
Command and Control
In the third phase of the kill chain, it's all about to command and control your footsteps inside the targets network.
Target: Control compromised client
Typically used protocolls: HTTPS, HTTP, SMTP, DNS (91.3%)
DNS useful if malware not yet knows what the IP of the C2C server is.
DGA (Domain Generation Algorithms) are used to transfer data from the targets network to the CnC servers. These are possible ways of detection:
- long rubish domains (entropy)
- negative answers (NX DOMAIN)
CnC Commands in pictures and posts on Twitter for example. It's not blocked and has a good reputation. -> Stegonagraphy. So you would have to block Twitter to stop the connection to the CnC from inside your network.
Encryption
TLS Decryption Challenge: Certificate Pinning. Client (Browser, but more in Apps) knows what Certificate to expect. Stopping MITM Attacks or MITM from the company.
- HTTP2 only with TLS because they don't wanted to use HTTP2 without TLS.
- HTTP2 allows the server to push data to the client.
QUIC protocol makes even faster, because TLS handshakes are slow and are only overhead. All Google pages are running this and it supports multipathing.
Defend against CnC
- IPS signatures on known bad CnC data content
- IP based reputation
- Block known bad DNS records
What to do when you not know the CnC?
- DNS names looks like DGA name
- DNS response with short TTL
- DNS to dynamic IP address
- Frequent DNS requests to non existent domains (NX-DOMAIN)
If you see this kind of requests, your client is already compromised.
DNS Sinkhole: Answer the request yourself with your own IP of a sinkhole server and not from the internet and see who access your sinkhole IP address.
Lateral Movement
In this phase of the kill chain it's about starting to move around in the targets network and do some more attacks on specific systems you want to get in your control.
Against IoT
IoT => Most valuable assets in an organization. For example in these industries:
- Healthcare
- Airport
- Manufacturing
These IoT devices suffers mostly::
- Unpatched Windows XP
- Old/Unpatched Linux
- Missing updates from the vendor
If you know the version of the OS you can search for exploits. With meterpreter you then access them and run a privilege escalation to the root access to the IoT device.
Against Active Directory
Huge topic. Get password and hashes. Ultimate target is the Domain Controller.
Weaponizing PowerShell
Key logging, screenshots, CnC, grab passwords and hashes (mimikatz) Powerful leverage WMI, .NET, Win32 and do almost everything on Windows.
Hashes One Way -> Chicken -magic -> chicken nuggets
We need never a password to authenticate so the hash is enough, which resides on the machines memory. Username is sent plaintext by the client with NTLM! Local admin rights (root) is only needed to read out the hash from memory with Mimikatz.
LSASS manages these hashes and the kerberos integration on the Windows OS.
With Powershell Empire:
- User Hunter (look for users in AD)
- to find out what machines the user has logged in to, so we can read out the hash from it
- Run mimikatz and get the hashes
- Login on the DC
- Run Mimikatz again to dump everything
- Get the KRBTGT hash!
- If they got it, every password and the DC needs to be changed!
- KRBTGT is the worst case for an organization! Changes almost never. Maybe on feature upgrades of AD..
Defend against this
- Only allow Keberos and not NTLMv2!!!
- Win10 Enterprise 64 Bit can run LSASS in an sandbox style to protect it. => Credential Guard
Movement in the Datacenter
Mostly there is no segmentation in the network. This is needed for visibility what happens between groups of machines while talking to each other (Firewall Logs). As well they cannot access machines where they don't need to.
Get Persistence
This is the second last step. The attacker will setup some ways of access to the targtes network to stay there as long has he wants to. Even if some evidence is found and some clients gets destroyed after that, the attacker want to stay in the targets network. After this phase, he can get his objectives done as planed.
He will try to get a Golden Kerberos Ticket. Here you find out more about Golden Tickets
An attacker may try to use File-less persistance to avoid AV detection.
Defend Summary
Same budget for user education than for the security technology!